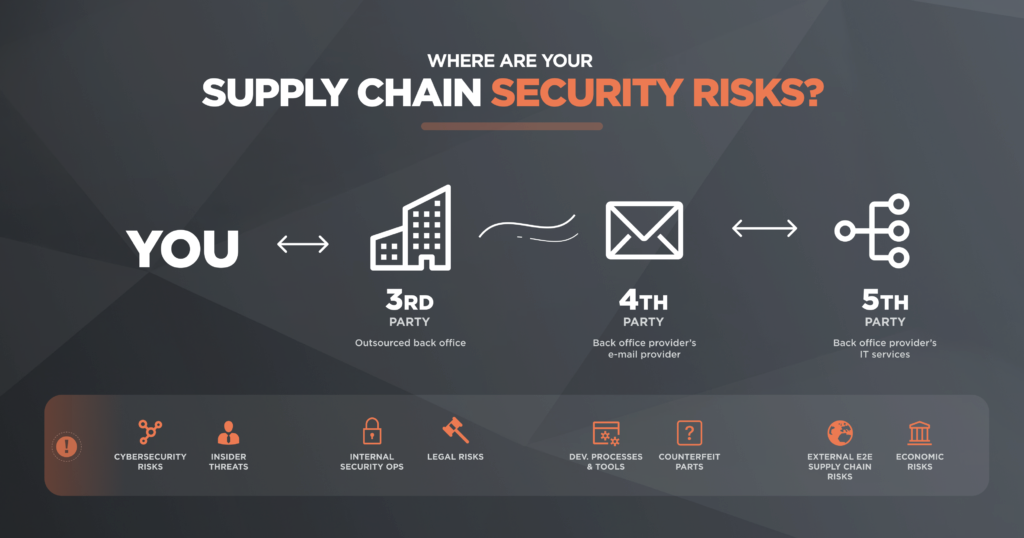
Cybersecurity supply chain risk management (SCRM) is the process of identifying, assessing, and mitigating cybersecurity risks associated with the supply chain, which refers to the interconnected network of organizations, processes, and systems involved in the production, distribution, and maintenance of goods and services.
In the context of cybersecurity, the supply chain can be vulnerable to various risks, such as cyber threats, malicious activities, and vulnerabilities in the hardware, software, or services procured from external vendors or suppliers. These risks can potentially compromise the confidentiality, integrity, or availability of data, systems, or services, and can have serious consequences for organizations, including financial loss, reputational damage, and operational disruptions.
Cybersecurity SCRM involves implementing measures to proactively manage and mitigate these risks throughout the supply chain lifecycle, from procurement and sourcing to delivery, deployment, and ongoing maintenance. This includes activities such as:
Risk assessment: Identifying and assessing cybersecurity risks associated with the supply chain, including evaluating the security posture of vendors and suppliers, analyzing potential vulnerabilities and threats, and assessing the potential impact of supply chain risks on an organization's cybersecurity posture.
Vendor/supplier management: Implementing measures to select and manage vendors and suppliers based on their cybersecurity practices, including conducting due diligence, establishing contractual requirements for cybersecurity, and monitoring the security performance of vendors and suppliers.
Supply chain monitoring: Continuously monitoring the security of the supply chain, including monitoring for cybersecurity incidents, vulnerabilities, and threats in the hardware, software, and services obtained from vendors and suppliers.
Incident response and recovery: Developing and implementing plans to respond to and recover from cybersecurity incidents or disruptions in the supply chain, including incident response plans, business continuity plans, and disaster recovery plans.
Security controls: Implementing appropriate security controls and best practices within the supply chain, such as encryption, authentication, access controls, and security testing, to reduce the risk of cybersecurity incidents.
Training and awareness: Providing training and awareness programs for employees, vendors, and suppliers on cybersecurity best practices, policies, and procedures related to the supply chain.
Compliance: Ensuring compliance with relevant laws, regulations, and industry standards related to supply chain cybersecurity, such as NIST Cybersecurity Framework, ISO 27001, and others.
Cybersecurity SCRM is critical for organizations to effectively manage and mitigate cybersecurity risks associated with their supply chain and ensure the security and resilience of their systems and data. It involves a holistic approach that requires collaboration and coordination among various stakeholders, including procurement, IT, security, legal, and other relevant departments, as well as strong partnerships with vendors and suppliers to collectively manage cybersecurity risks throughout the supply chain ecosystem.
Comments
Post a Comment